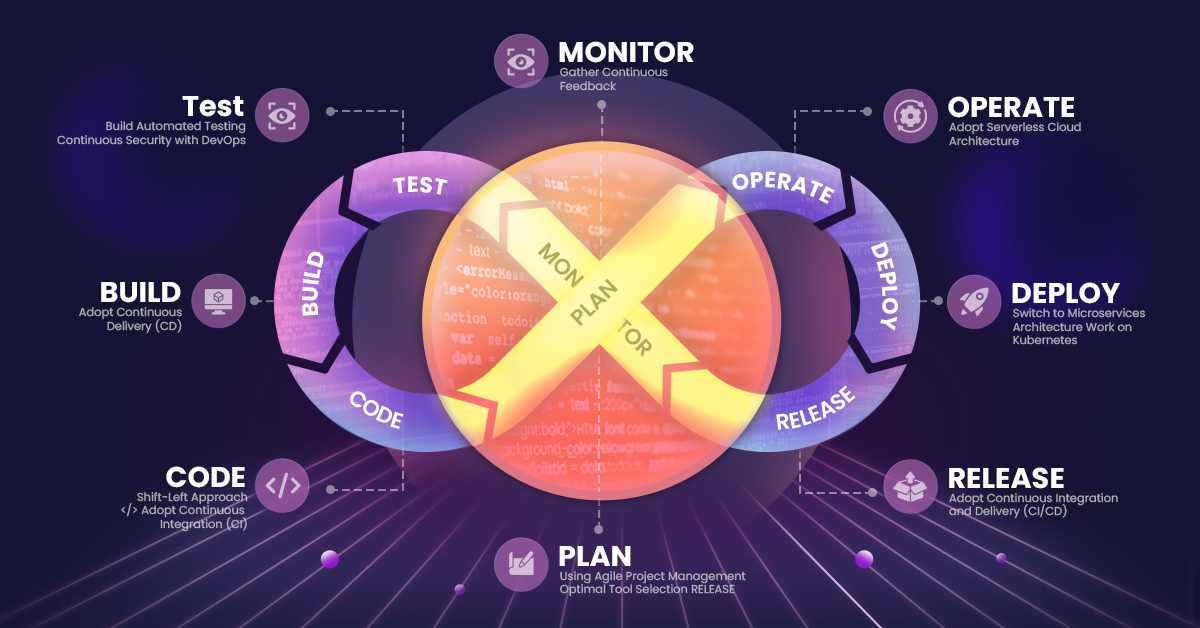
From DevOps To DevSecOps – Challenges & Best Practices

“While DevOps takes care of bringing a culture change at the workplace by breaking down the silos and bridging the gap between teams, DevSecOps aims in inducing the security aspects in early development cycle rather than pushing it on end of the pipeline”
The popular trifecta “Dev+Sec+Ops’ is on high demand among the Enterprises no matter whether they are a small players or IT giants in the global market. In the devops world, often the security is overlooked!
While the Enterprises and DevOps Engineers are busy moving towards the DevOps culture, hackers on the other hand are trying their best to deploy the bad stuff like malware and other unauthorized activities in the application.
In a developer-centric world, the interesting thing about DevSecOps is they bring together the security team to work in alignment with the developmental and operations teams and make them realise that security is not a one-man army that it should be implemented from the beginning of a software development life cycle.
What are the challenges we face while adopting a DevSecOps culture?
Before looking in the best practises, let’s talk about some of the pain points that an Enterprise would face while adopting a Secure devops methodology!
One of the biggest Devops challenges is, the IT Security teams need to get upto the speed when planning a DevOps integration for your workplace. With the frequent deployments of the software application which is the nature of the DevOps implementation, the Security guys must adapt to the faster developmental life cycle.
Changing to High security tools where most of the developers find it difficult with a resistance to change is a common development and operational challenge every company faces. Upskilling of the security professionals is lagging where their lack of knowledge often leads to a slower bug fixing which risks the overall deployment process to slow down.
Usually, security checks are often checked at the end of a software pipeline where almost all the coding had been built and ready to be deployed in the production. But finding out error at this stage, will stress out the developer which will make them to do patching as a temporary fix rather than finding a permanent solution.
“Rome was not built overnight, so is the DevOps implementation process for any Enterprise. One of the main challenges in DevOps implementation is to change the age old legacy systems into DevOps culture in a safe and secure way”
Real-World Success Stories of DevSecOps Across various industries
Logistics – Document Logistix provides a shared platform which has customer sensitive information. Introducing DevSecOps provided an automated application process that is secured.
Banking – HSBC through ‘Transformation Alpha Project’ had reduced the ‘compliance lead time’ by adopting DevSecOps method where their security engineers pulled it off seamlessly during any massive unplanned security slowdowns
Insurance Sector – Allianz did a successful DevSecOps pilot project which showed significant results by 20% sales increase in first week, shorter time for bug fixing with shift testing, data classification and so on.
Best Practises for DevSecOps
Here are a few tried and tested DevSecOps practices that helps in creating a secure software application from build to deploy with no possible vulnerabilities or malware attacks. There are several DevOps tools to monitor the application during the CICD workflow. However, some security tools also helps in implementing the DevSecOps process.
Best Practise 1 – Get Started with a Common Weakness Enumeration List
What if we told the developers who are constantly facing some security issues that they are not alone! As we all know, to err is human which means developers too are no exceptions from making any errors while coding, CWE is created for helping and educating the developers.
What does CWE mean and how does it work?
Basically it is a community built for developers who can find solutions for commonly found security issues and weakness associated with certain tools, DevOps security checklists and quickly find a fix for it.
This portal allows you to search the common software weaknesses by three categories,
By research concepts
By Development Concepts
By Architectural Concepts
For example – In some cases, there maybe J2EE misconfiguration where data may be transformed without proper encryption. Like some attackers may intentionally divert the users to login through insecure URL.
Hence, during the system configuration step, the configurations of all the applications must ensure that they follow a robust encryption mechanism should be followed in all the website pages.
Best Practise 2 – Code It Simple and Make it Readable!
“2014 was not so promising for automobile industry which saw several hundreds and thousands of vehicles recalled! Similarly, in 2017 FDA cancelled licenses for a massive number of medical devices!! All for a single same reason – software hacking and security breaches ”
Writing Code in simple, readable format is essential. As implementing security starts with your code in the development stage itself. A snippet of code should be created in such a way it should be easily understood by other developers without a need to explain to them what it is intended for or why it is used.
Content inside the image : VPNFilter malware reports that it affected nearly 500,000 routers and NAS devices in May 2018.
For example – MISRA is a set of coding standards which provides the best coding practices for programming languages like C and C++ such as,
Do not use too much of parentheses which decreases the readability of the code.
NULL must not be replaced by an integer value and so on.
In a nutshell MISRA works as follows,
Runs a thorough scan of your code
Coding Standard is applied like MISRA
Creates a standard Checklists to know if the code meets the security standards
Improves the code quality
Finally, it helps to reduce the time and cost
Best Practices 3 – Shift Left Method in DevSecOps
Imagine a scenario where you develop a code and it is moved to testing environment and later on passed to the production environment. But unexpectedly it throws some security threats and breaches in the later stage of the deployment in a production environment where almost 80% of the development work might have been completed.
In fear of the re-writing the whole chunk of code from starting, we may comprise on the quality of the code like doing some patching of fixing the code temporarily which will eventually backfire throwing defects in the end product of the software product.
This is where ‘Shift Left’ concept in DevSecOps comes into play. As soon as you start working on your coding part in the development part, the security features also triggered simultaneously which will scan all your coded then and there, giving no room for last-minute surprises.
Using Static Application Security Testing tools (SAST) is your best bet. Because, choosing the right Devops security tools and using it wisely might seem like a little daunting tasks. Helix QAC is a popular and widely used SAST tool where it continuously checks your code for any bugs and gives you instant feedback to rectify the error.
“The more frequently you check for any vulnerabilities in your code, the more efficient and reliable your codebase will be”
These DevSecOps best practices presented here it’s just a starting point to move from a DevOps process to a DevSecOps method by following certain security practices along the developmental process. Keep watching this place, where we intend to include more best practices as and when new threats are introduced! Yeah I know , with increased technology, keeping the security threats totally at bay is impossible but implementing a Devsecops surely will keep you going without deviating from the core idea of Devops – “the speed software delivery” to your customers!